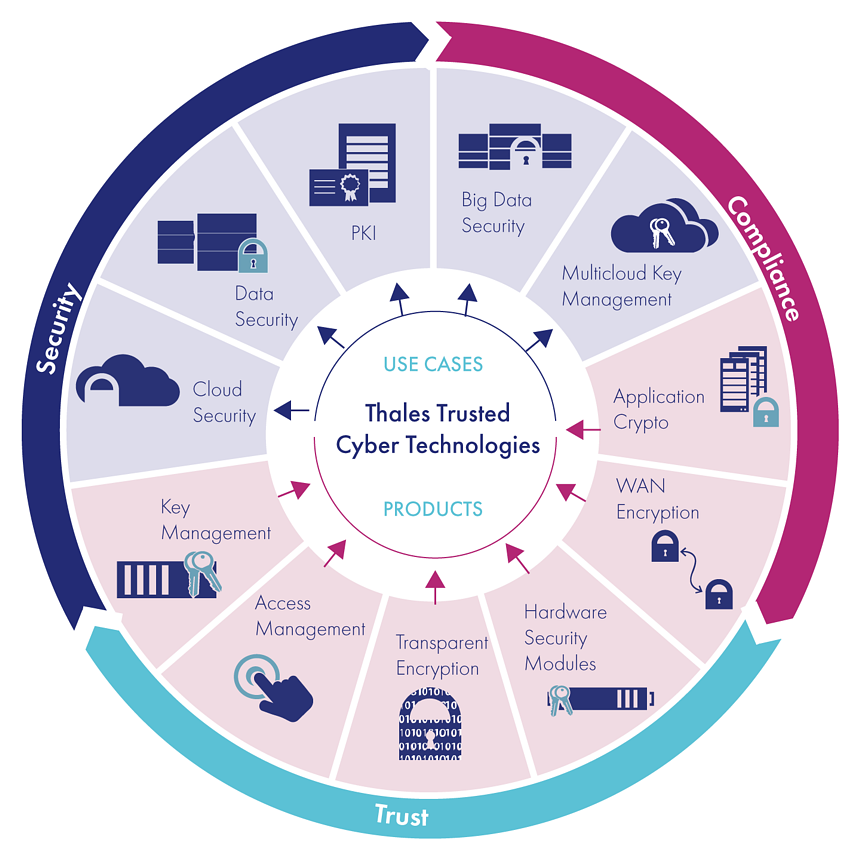
Thales Trusted Cyber Technologies (TCT) is a U.S. based provider of government high-assurance data security solutions. Our mission is to provide innovative solutions to protect the most vital data from the core to the cloud to the field for defense, intelligence, and civilian agencies across the U.S. Federal Government. With a concentration on Federal and other U.S. government agency requirements, Thales TCT is better able to serve its government customers while also investing in the development of future technologies to secure the Federal Government’s most sensitive information.
Our Story
On January 1, 2020, SafeNet Assured Technologies, LLC. and Thales Cloud Protection & Licensing, Federal united under a new name as Thales Trusted Cyber Technologies, a division of Thales Defense and Security Inc. Our employees are dedicated to providing the most secure products in the industry. Many of our employees have over 20 years of experience in designing and manufacturing data security products for both government and commercial applications dating back to the original IRE and SafeNet, Inc. days.
Challenges We Solve
We offer best-of-breed solutions to our U.S. Federal customers. From our core solutions developed specifically for the government to Thales Cloud Protection & Licensing commercial-off-the-shelf solutions we sell and support, our offerings address the most stringent federal requirements. Our extensive data security experience allows us to provide one of the most broad data protection portfolios specifically focused on U.S. Federal agency requirements for protecting mission critical data in data centers, cloud environments, and field deployments.